AWS Lambda SnapStart
Here is the Lambda execution environment lifecycle:
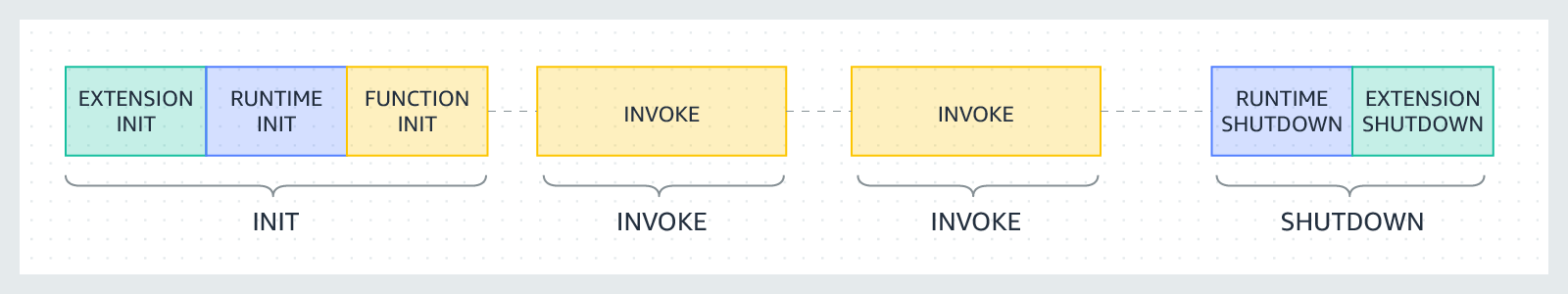
Each phase starts with an event that Lambda sends to the runtime and to all registered extensions. The runtime and each extension indicate completion by sending a Next API request. Lambda freezes the execution environment when the runtime and each extension have completed and there are no pending events.
And this illustrates latency during the cold start:
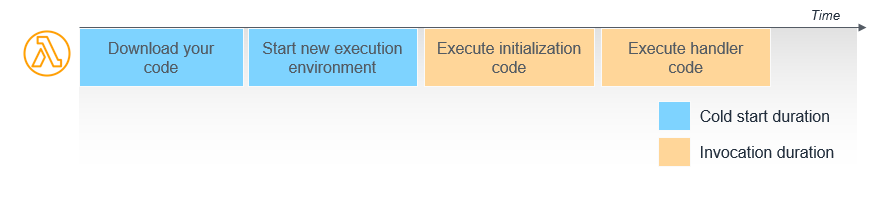
SnapStart is a feature that optimizes the initialization phase by taking a snapshot of the function's execution environment after initialization is complete. When a new invocation occurs, Lambda restores the snapshot, allowing the function to be invoked immediately without reinitialization.
This approach significantly reduces the cold start latency that can affect performance-sensitive applications.
Currently, it is available for newer versions of Java/Python/.NET-based runtimes, and other managed runtimes (such as nodejs22.x and ruby3.3), OS-only runtimes, and container images are not supported yet.
Activating SnapStart
To enable SnapStart for your Lambda function, follow these steps:
Using the AWS Management Console:
- Navigate to the AWS Lambda console.
- Select your function.
- Go to the Configuration tab and choose General configuration.
Click Edit, set SnapStart to Published versions, and save the changes.
- Publish a new version of your function.
Using the AWS CLI:
Run the following commands to enable SnapStart for your function:
aws lambda update-function-configuration --function-name my-function --snap-start ApplyOn=PublishedVersions
aws lambda publish-version --function-name my-function
Replace my-function with your function's name. After publishing, SnapStart will be active for that version.
Maintaining Uniqueness with SnapStart
Since SnapStart restores functions from a snapshot, any unique data generated during initialization (like unique IDs or random numbers) will be duplicated across invocations. To ensure uniqueness:
- Generate unique data within the function handler, not during initialization.
Use cryptographically secure random number generators (CSPRNGs) to maintain randomness.
Example #1 in Python:
In this example, a unique ID is generated each time the function is invoked, ensuring uniqueness across invocations.
import json
import random
import time
unique_number = None
def lambda_handler(event, context):
seed = int(time.time() * 1000)
random.seed(seed)
global unique_number
if not unique_number:
unique_number = random.randint(1, 10000)
print("Unique number: ", unique_number)
return "Hello, World!"
Example #2 in Python:
Or, you can use a CSPRNG to generate random numbers securely:
import json
import random
secure_rng = random.SystemRandom()
def lambda_handler(event, context):
random_numbers = [secure_rng.random() for _ in range(10)]
for number in random_numbers:
print(number)
return "Hello, World!"
Using Runtime Hooks in Python
AWS provides runtime hooks that allow you to execute code at specific points during the snapshot lifecycle:
@register_before_snapshot: Runs code before the snapshot is taken.
@register_after_restore: Runs code after the snapshot is restored.
Example:
from snapshot_restore_py import register_before_snapshot, register_after_restore
@register_before_snapshot
def before_snapshot():
# Code to run before snapshot
print("Running before snapshot")
@register_after_restore
def after_restore():
# Code to run after restore
print("Running after restore")
def lambda_handler(event, context):
print("Handler execution")
# Your handler logic here
This setup ensures that specific code runs at the appropriate stages of the snapshot lifecycle.
Monitoring SnapStart Functions
Monitoring is crucial to ensure your SnapStart-enabled functions perform as expected. You can use Amazon CloudWatch and AWS X-Ray for this purpose.
CloudWatch Logs:
CloudWatch provides logs for both initialization and invocation phases. For SnapStart functions, you'll see an INIT_REPORT log entry detailing the initialization duration.
X-Ray Tracing:
With X-Ray, you can trace requests to your functions. In SnapStart functions, the Restore subsegment indicates the time taken to restore the snapshot and execute any after-restore hooks.
Security Considerations
SnapStart supports encryption at rest. By default, AWS Lambda encrypts snapshots using an AWS managed KMS key. If you prefer, you can specify a customer-managed KMS key during function configuration:
aws lambda update-function-configuration --function-name my-function --kms-key-arn arn:aws:kms:region:account-id:key/key-id
Replace my-function with your function's name and provide the appropriate KMS key ARN.
Best Practices for Optimal Performance
To get the most out of SnapStart:
- Preload dependencies and initialize resources during the initialization phase to reduce latency during invocation.
- Organize your code efficiently, ensuring that heavy computational tasks are handled during initialization.
- Use runtime hooks to manage tasks that need to occur before snapshotting or after restoring.
Example in Python:
# Import all dependencies outside of Lambda handler
from snapshot_restore_py import register_before_snapshot
import boto3
import pandas
import pydantic
# Create S3 and SSM clients outside of Lambda handler
s3_client = boto3.client("s3")
# Register the function to be called before snapshot
@register_before_snapshot
def download_llm_models():
# Download an object from S3 and save to tmp
# This files will persist in this snapshot
with open('/tmp/FILE_NAME', 'wb') as f:
s3_client.download_fileobj('amzn-s3-demo-bucket', 'OBJECT_NAME', f)
...
def lambda_handler(event, context):
...
By preloading data during initialization, you reduce the time spent fetching resources during invocation, leading to better performance.
Conclusion
SnapStart is a powerful feature that significantly reduces cold start latency for AWS Lambda functions. By taking a snapshot of the function's execution environment after initialization, SnapStart allows functions to be invoked immediately without reinitialization. This feature is available for newer versions of Java/Python/.NET-based runtimes and can be enabled through the AWS Management Console or CLI. To maintain uniqueness, generate unique data within the function handler and use CSPRNGs for randomness. Runtime hooks can be used to execute code at specific points during the snapshot lifecycle. Monitoring with CloudWatch and X-Ray is essential to ensure optimal performance, and security considerations include encryption at rest. By following best practices and optimizing your code, you can leverage SnapStart to enhance the performance of your Lambda functions. Remember, SnapStart will not boost startup time if the function is already warm, and might not be as effective for functions that are invoked infrequently.

